Summary
This article will outline the various ways in which the player can deal with the Integrated Air Defence System as simulated within BMS. Please note that despite some parallels between real life strategy and strategy in BMS, this is not an operational manual, nor do I claim to know anything about the real-life theory of countering IADS. This article will be broken down into; a description of what an IADS is, a summary of historical examples, the components likely to make up an IADS and finally a generalised guide on the various methods of defeating an IADS.
What is an IADS?
The acronym IADS is the contraction of ‘Integrated Air Defence System’. The IADS is the branch term used when discussing the ‘structure, equipment, personnel, procedures, and weapons used to counter the enemy’s airborne penetration of one’s own claimed territory’.[1] Put simply, a nation uses an IADS to coordinate the defence of its sovereign or seized airspace. The components of an IADS system vary from nation to nation but the complexity and variety of systems simulated within BMS allow this to be drastically simplified. For example, currently there are no sophisticated electronic warfare (EW) systems simulated in BMS which is a major factor for discussion in real operations.
However, where BMS does not deviate from real life is in the simulation of the Early Warning Radar (EWR) sites, the employment of Surface to Air Missile systems (SAM), and coordination between airborne early warning craft (AWAC) and fighter aircraft. All these assets work together in one integrated system to prevent you from breaching enemy airspace and completing your mission.
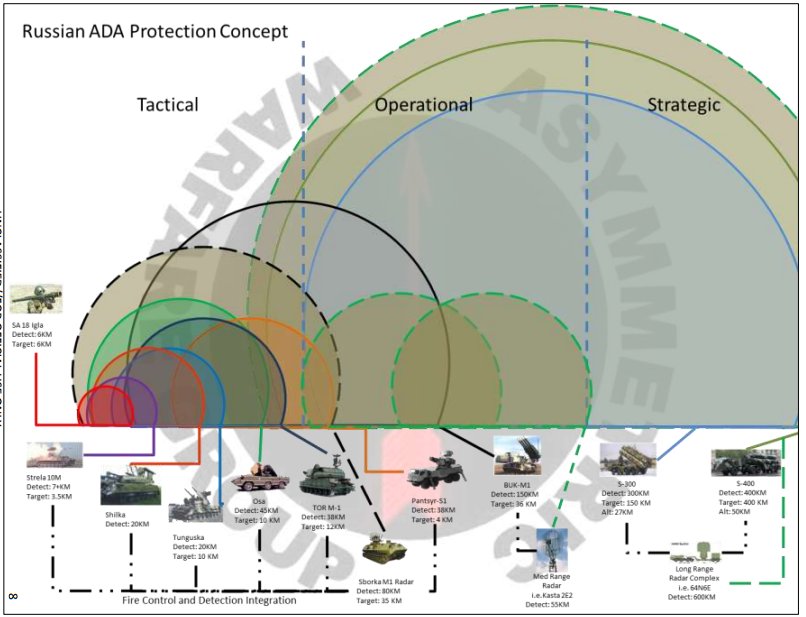
The IADS in History
Air defence has been a critical factor in warfare since the dawn of air power. As retired USAF Col. John A Warden III stated, ‘No country has won a war in the face of enemy air superiority… no major offensive has succeeded against an opponent who controlled the air, and no defence sustained itself against an enemy who had air superiority’. This quote has remained true to this day and multiple historical examples can be found throughout history. From the defence of the United Kingdom in WW2 to the stunning Israeli victory in the 6 Day War and the annihilation of the Iraqi armed forces in both Gulf Wars.
Again Col. Warden III provides us with a justification as to why IADS have become such a prominent feature in modern and past conflict – ‘Attaining air superiority has consistently been a prelude to military victory’. This meshes with the primary purpose of the IADS, to prevent the enemy from penetrating your air space and gaining air dominance over your own forces.
Components of an IADS
Quite simply the components of an IADS are the structures, procedures, equipment, and weapons that make up the umbrella of the IADS. This articles scope is limited to the depiction shown in BMS thus personnel will not be considered in full details. An IADS will be structure around air surveillance (EWR, AWAC, Intelligence), Battle Management (C2 and Networking), and Weapons Control (FCR, Launchers).
- Air Surveillance consists of.
- Detect
- Initiate
- Identify
- Correlate
- Maintain
Air Surveillance begins with the detection of an enemy aircraft entering the IADS area of responsibility. The initiate function moves the detection into tracks, these tracks are then subjected to the identify phase. The identification of tracks using IFF procedures to ascertain the identity of the track. Correlation refers to the sanitation of the air picture using command and control elements of a modern networked IADS. For example, multiple different radar systems may have detected the same track moving into the covered air space, the correlate phase will then be used to determine if these tracks are the same contact or three different contacts. Finally, the maintain phase simply refers to the multiple different tracks being monitored, this may allow for a handoff onto a weapons system or just to observe the tracks behaviour. The maintain function in a modern IADS can be largely automated which largely removes ‘man-in-the-loop’ factors and allows for more effective decision making by the IADS commanders.

- Battle Management includes.
- Threat evaluation
- Engagement decision
- Weapon selection
- Engagement authority
These steps are largely self-explanatory. Threat evaluation involves the classification of the threat and thus allows for the relative danger posed by said threat to be understood in the wider context of the situation. This evaluation is based on but not purely limited to range to target, known capabilities, behaviour, and position. Put simply, an IADS would choose to engage a cruise missile closing on its target over the small drone doing reconnaissance. Threat evaluation will factor heavily in the engagement decision, as aforementioned the highest threat targets will be engaged first. Weapon selection is another transparent step, different weapon systems will be designed to counter different threats. Finally, Engagement Authority is simply the final step in the decision to engage a target.
Weapons control relates – unsurprisingly – to the systems and equipment used to guide and control weapons such as Fire Control Radars (FCR), individual elements like Transporters, Erectors and Launchers and combined systems such as Transporter Erector Launcher and Radar systems (TELAR) systems. Broadly, these systems facilitate the firing and guidance of weapons to interception.
How to defeat an IADS
This section will outline a selection of methods that will help you in your understanding of how to defeat an IADS. Most importantly, it is not always necessary to destroy large sections of an IADS to achieve your mission objective. Thus, it is critical to completely understand your mission and what risks you are willing to accept in achieving it.
It is often possible to achieve a penetration of enemy airspace with minimal effort dedicated towards degrading the components of the enemy IADS. This can be achieved through means such as stealth, electronic warfare (jamming), flight profiles (low level) and the simple measure of just avoiding heavily monitored/contested areas. Tactics such as these are often employed on missions where limited penetration allows the objective to be completed such as air interdiction on the FEBA, strikes on battlefield logistical nodes and other tasks like these.
However, such luxury only extends so far. For many missions it will be necessary to degrade or destroy significant areas of the enemy IADS. There are several methods of achieving this with the broad subcategories being hard and soft defeat. Hard defeat methods are best characterised by kinetic means – in simple terms, blowing equipment up and killing personnel to permanently degrade or destroy sections of the IADS. Soft defeat includes non-kinetic means like Electronic Warfare (EW) and Intelligence Surveillance and Reconnaissance. Understand that these methods are not binary and often it is prudent to blend both soft and hard defeat tactics into the planning for your mission.
Hard Defeat Methods
To effectively destroy a portion of an IADS network you will first need a solid understanding of the enemy’s disposition and what structure their network follows. When dealing with older style networks (like the one in the default KTO) you can significantly degrade the enemy IADS by targeting their fixed command and control node (C2), early warning radars (EWR) and supply depots. This will significantly complicate any efforts by enemy IADS commanders to coordinate the actions of their network due to them either being killed at their C2 stations, being blinded at long range due to not having EWRs and, not being able to resupply their missile units.
After degrading the ability of hostile forces to coordinate and have early warning capability they will be forced to illuminate from their higher value systems like the search radars attached to SAM sites like P-12 ‘Spoon Rest’. This will aid you in the detection and localisation of fixed sites such as SA-2/3/5 and allow for their suppression or destruction. Now that you have kicked in the door and can begin to trespass into enemy airspace, you must again consider your mission – are you out there to perform DEAD and permanently destroy enemy SAM threats to provide safe passage for larger less manoeuvrable assets such as B-1 or B-52 or are you escorting a package with a specific threat that needs to be destroyed due to the danger it poses? The answer to this assessment will inform you of what needs to be done.
.jpg)
If you are waging a campaign to significantly degrade the hostile IADS then the continued localisation and destruction of enemy SAM sites and associated equipment is mandatory. The timeline for this should be as rapid as possible, the destruction of EWR, C2 and SAM sites can be simultaneous or if you’re limited in airframe numbers then the priority of destruction should be EWR and C2 simultaneously followed by the SAM sites themselves.
When dealing with a significantly more modernised IADS such as those present in the ITO and NTO simply pursuing hard defeat tactics becomes significantly more complicated. Area denial systems such as SA-17 and SA-10 are significantly more deadly to tactical aircraft when compared to their older cousins. Because of this, there is a much higher risk factor when deciding to kinetically engage these systems which must be factored into mission planning. These systems not only have better probability of kill on a fighter sized target, they are also less dependent on external early warning radar sites due to their more advanced multi-purpose radars which often combine search and track functions. Due to the aforementioned factors, it is recommended that standoff weapons such as JSOW, JASSM and SDB are used to destroy these sites. This task is further complicated by the more mobile nature of modern IADS components, this necessitates prudent ISR coverage using assets like JSTARS to keep track of where these assets are moving at to provide up to date targeting information for standoff weapons regardless of if they possess ‘Man In The Loop’ (MITL) capabilities like SPICE and SLAM-ER.
Soft Defeat Methods
Thankfully, there is much less to consider when discussing soft defeat methods in BMS due to the limitations of classified material and what is implemented in BMS. Other than simply avoiding the elements of an IADS, the primary method of soft defeat in BMS is using onboard and offboard jamming. While the implementation of jamming in modern flight sims is basic, BMS does possess an adequate representation of the basics of this type of electronic warfare (EW) and learning how to effectively use the dedicated platforms is critical to success in BMS.
On-board jamming is a double-edged sword, and this is reflected in BMS, while this jamming does degrade the effectiveness it also clearly displays your presence to the enemy because of the high energy emissions coming from the aircraft. The F-16 can mount a centreline jammer and more modern blocks have internal jammers which work on this “sweep jamming” principal.
Off-board jamming refers to using a dedicated jamming platform such as the EA-18G, EF-111 and the Tornado ECR. These platforms have incredibly powerful jamming capability and can shutdown large segments of the enemy radar network. Unlike smaller onboard jammers, the large, dedicated units used by these platforms are capable of extremely high-power output and can dedicate such energy targeting specific radars – rendering them useless instead of degrading them. In BMS these platforms create a bubble in which enemy radars are essentially disabled and cannot be used to engage you. This is an incredibly powerful capability and will create a permissive environment to strike at key enemy targets without interference from SAM sites. The downside to dedicated EW platforms is that they are a high value asset which are forced to trade the advantages of manoeuvrability and self defence for their jamming capability. The only minor exception to this role is the EA-18G which retains the capability to employ AIM-120 from its belly stations – however, only two can be carried. This means that your mission must include elements to protect the jamming aircraft, or you risk losing the protection it provides.
Lastly, stealth/low observable platforms are also modelled in BMS. While rare and very valuable, these aircraft are capable of penetrating deep into enemy airspace without supporting assets. Much like in the 1991 Iraq war where USAF F-117s were able to strike deep into the heart of the Iraq despite the substantial Iraqi IADS, the same is possible in BMS. In theatres where stealth aircraft are widely proliferated such as the NTO and some modified Korean campaigns stealth aircraft should be primarily used in the deep strike role to destroy very high value targets within enemy territory like powerplants, headquarters, primary communication nodes and air bases. After this has been conducted, their further use will depend on what the platform is. For example, the F-22 in BMS will quite happily obliterate most other aircraft in the BVR environment while remaining undetected and the F-35 in BMS is still a capable multirole platform to be used in whatever mission is needed.

Example Blended Soft / Hard Mission
The process of planning and executing a strike mission into an area protected by an IADS will now be outlined. This hypothetical mission will be a strike on an enemy C2 node located some distance behind the FEBA and protected by a near peer air defence network.
A good mission can only be obtained through good intelligence and surveillance in the days leading up to the strike. The location of threat systems must be known, and their capabilities understood as this will affect the decision-making process of all parties. Once thorough reconnaissance has been conducted the next step in proper planning is the allocation of assets, in this instance we have located a particularly nasty threat system close to the C2 node – an SA-11. This system is deemed an extremely high threat and likely to impede mission success, so it has been designated for disruption and destruction. To do this we must first get close to the SAM without it having warning of our presence until it is too late, thus the mission commander has elected to use a blended soft/hard defeat method when dealing with the wider IADS and the SA-11 specifically. To breach enemy airspace and avoid early warning strikes have been conducted in the days leading up to the mission to degrade and disable two prominent EWR sites in our path. Furthermore, the mission also includes a dedicated SEAD element with EW support provided by a jamming aircraft (EA-18G) to shut down any unknown pop-up threats and to degrade the SA-11. Finally, before the strike flight drops weapons on the C2 node a dedicated DEAD flight is scheduled to arrive 10 minutes before and destroy the SA-11 TELARs and dedicated radar vehicle to permanently remove the threat.
To account for any air activity and defend the jamming platforms a flight of F-22s will penetrate the enemy airspace using their stealth capabilities to operate well forward of the strike package and prevent interception by the enemy QRA assets. While the F-22s go deep into enemy airspace on the sweep mission, escort for the package will be provided by the ever-reliable F-15Cs due to their high endurance and weapons load. Overall situational awareness for the mission will be provided by an AWACS (E-3).
This is a basic example of a possible mission structure of a strike mission within a wider air campaign. Please note the thought process which can be applied to any type of mission due to it accounting for the structure of friendly forces and capabilities as well as considering enemy systems and capabilities. The most powerful weapon at your disposal in BMS is your knowledge. Understanding what you can do, but also what the enemy can do to you is the key to success.
Bibliography
- Col. (Ret) Craig R. Corey, The Air Forces Misconception of Integrated Air and Missile Defence, Air & Space Power Journal, Winter 2017, pp. 81 – 90.
- John R. Hoehn, Integrated Air Defence Systems (IADS) and Military Ranges, Congressional Research Service, 24th February 2021.
- Joint Publication 3-01, Countering Air and Missile Threats, 2017.
- Justin Bronk, Modern Russian and Chinese Integrated Air Defence Systems, RUSI Journal Occasional Paper¸ 2020.
- Website – https://www.airforcemag.com/article/what-is-a-modern-integrated-air-defense-system/ – accessed 30/07/2021
[1] Website – https://www.airforcemag.com/article/what-is-a-modern-integrated-air-defense-system/ – accessed 30/07/2021





